HEADLINE CYBERCRIMES-POLITICS | FBI Takes Down Massive Army Of ‘Zombie’ Computers
A Chinese citizen running the world’s largest botnet was arrested.
A Chinese citizen running the world’s largest botnet was arrested.

WASHINGTON – An international law enforcement team has arrested a Chinese national and disrupted a major botnet that officials said he ran for nearly a decade, amassing at least $99 million in profits by reselling access to criminals who used it for identity theft, child exploitation and financial fraud, including pandemic relief scams.
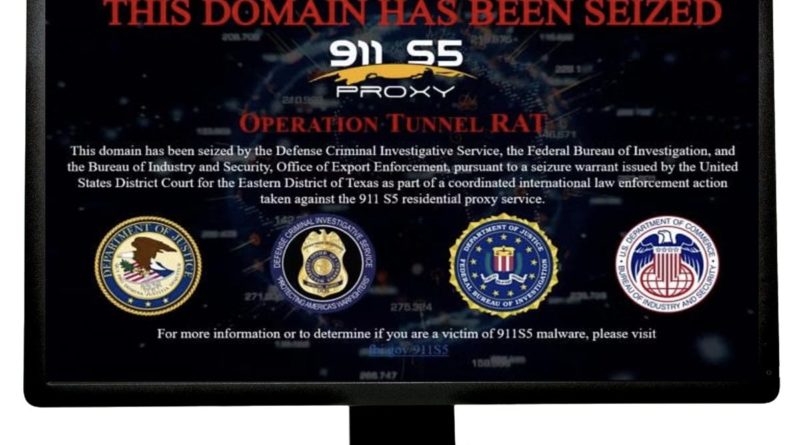
The US Department of Justice quoted FBI Director Christopher Wray as saying Wednesday, May 29, that the “911 S5” botnet – a network of 19 million malware-infected computers in nearly 200 countries – was likely the world’s largest.
In a news release, the department said Yunhe Wang, 35, was arrested on May 24.
Brett Leatherman, FBI deputy assistant director for cyber operations, said in a LinkedIn post that Wang was arrested in Singapore and that search warrants were executed in Singapore and in Thailand.
Leatherman added that authorities also seized $29 million in cryptocurrency and about $30 million in real estate.
The indictment says Wang used his illicit gains to purchase 21 properties in the US, China, Singapore, Thailand, the United Arab Emirates and St. Kitts and Nevis, where it said he obtained citizenship through investment.
Cybercriminals used Wang’s network of zombie residential computers to steal “billions of dollars from financial institutions, credit card issuers and accountholders, and federal lending programs since 2014,” according to an indictment filed in Texas’ eastern district.
In announcing the takedown, US Attorney General Merrick Garland said Wang, as the administrator, sold access to the 19 million Windows computers he hijacked – more than 613,000 in the United States – to criminals who “used that access to commit a staggering array of crimes that victimized children, threatened people’s safety and defrauded financial institutions and federal lending programs.”
Other violations tied to the botnet, according to the Justice Department, include bomb threats and cyberattacks.
Garland said criminals who purchased access to the zombie network from Wang were responsible for more than $5.9 billion in estimated losses due to fraud against relief programs.
Officials estimated 560,000 fraudulent unemployment insurance claims originated from compromised IP addresses.
Wang allegedly managed the botnet through 150 dedicated servers, half of them leased from US-based online service providers.
Botnets are created when cybercriminals install malware on computers or other connected devices and harness them for nefarious activities, creating a zombie army of devices whose owners are usually unaware of what is happening.
Leatherman said residential IP addresses became compromised when users downloaded certain free software or virtual private network (VPN) apps, which unknowingly contained mal-ware associated with the botnet onto their devices.
In its news release, the Justice Department thanked police and other authorities in Singapore and Thailand for their assistance.
Leatherman said the US is awaiting Wang’s extradition.
PNP shuts online services
In Manila, the Philippine National Police (PNP) is investigating recent data breach attempts on its systems and has shut down all its online services “until further notice.”
Col. Jean Fajardo, PNP chief publicist, said the shutdown is intended to give way to security measures to protect the PNP information technology infrastructure and to enhance its defensive postures against hackers after the data breach in the systems of two police units.
“In this regard, all PNP online services are temporarily unavailable until further notice. We regret any inconvenience this may cause,” Fajardo said.
On the shutdown of the largest botnet, a senior official of the PNP Anti-Cybercrime Group assured the public yesterday that they have not detected the botnet in the country.
“None so far,” the official, who spoke on condition of anonymity, said in a message on Viber. – With Emmanuel Tupas

@[email protected]

 Memento Maxima Digital Marketing
Memento Maxima Digital Marketing






