THE DAILY PLANET: U.S. Spy Plane Impersonates Malaysian Aircraft, Apparently to Fool China
.
.
.

- A U.S. Air Force RC-135W reconnaissance aircraft carried out several flights off China’s Hainan island.
- The plane switched its transponder code in mid-flight, mysteriously becoming a Malaysian airplane.
- The RC-135W was likely trying to keep a low profile while it spied on Chinese military bases.
.

A U.S. Air Force aircraft electronically impersonated a Malaysian plane while flying over the South China Sea this week. The RC-135W Rivet Joint reconnaissance aircraft flew off China’s Hainan island on Tuesday, coming within 55 miles of the Chinese mainland.
✈ You love badass planes. So do we. Let’s nerd out over them together.
The caper was outed on Twitter by a think tank operated by the Chinese government, which provided enough details for independent verification.
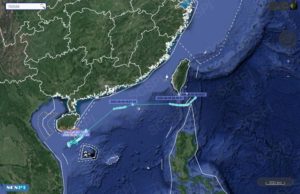
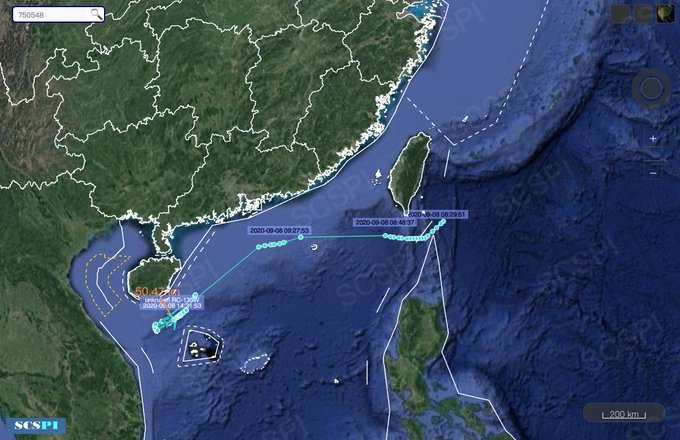
The Twitter account of the South China Sea Probing Initiative shared a pair of screenshots that showed a RC-135W take off from Kadena Air Base, a U.S. Air Force base on the island of Okinawa. The plane flew southwest, following the Ryukyu islands chain, past Taiwan, to loiter off the coast of Hainan Island.
The plane’s International Civil Aviation Organization (ICAO) Mode-S number, a 24-bit identifier assigned to all aircraft and broadcast by onboard transponder, was AE01CE. The Mode S system provides big-picture situational awareness and improves aviation safety.
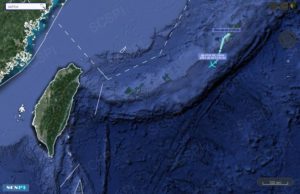
At some point, the plane’s Mode-S number suddenly changed, from AE01CE to 750548. That’s the ICAO number for an unknown Malaysian aircraft. The RC-135W, call sign RAINY51, then flew a racetrack pattern between Hainan Island and the Paracel Islands, an archipelago in the South China Sea that China claims, but whose ownership is in dispute. Here’s another screenshot from a plane-tracking app that shows the same flight:

.

The Most Badass RC Planes
Aircraft sometimes broadcast the wrong Mode S number, though that’s typically a mistake by the airplane operator. ICAO numbers aren’t supposed to be changed, as that degrades overall confidence in the system. But the idea that someone’s finger slipped and AE01CE accidentally became 750548 seems extremely unlikely.
The RC-135W Rivet Joint is a converted Boeing 707 jetliner designed to collect electronic intelligence for later analysis. The Air Force describes the jet as follows:
The Rivet Joint’s modifications are primarily related to its on-board sensor suite, which allows the mission crew to detect, identify and geolocate signals throughout the electromagnetic spectrum. The mission crew can then forward gathered information in a variety of formats to a wide range of consumers via Rivet Joint’s extensive communications suite.
It’s not clear why the RC-135W flew where it did. The flight probably coincided with Chinese military exercises, likely air or naval, or even a missile test. It’s also worth pointing out that China’s nuclear ballistic missile submarine force is based at Yulin on Hainan Island.
.

It’s also not clear why the RC-135W engaged in the deception. Steffan Watkins, a Canadian open source intelligence researcher, tells Popular Mechanics:
“If the reconnaissance is happening outside sovereign airspace, there is no pressing need to engage in that sort of deception. It’s perfectly legal, and done in plain sight off the coast of Russia, Syria, and Crimea all the time—literally, every day there are RC-135s off the coast of Russia, with their transponders on, and broadcasting exactly who they are. I can’t explain the difference with China. Why the difference in emissions posture and obfuscation?”
The South Sea Probing Initiative, a China-based think tank whose advisory board includes serving officers of the People’s Liberation Army and Chinese Navy, first announced the imitation, Still, it appears the data is correct. The announcement is likely a warning to the Pentagon that the Chinese military sees through the deception, and that it’s watching the watchers.
.